DDOS ATTACk
DDoS Attacks Explanation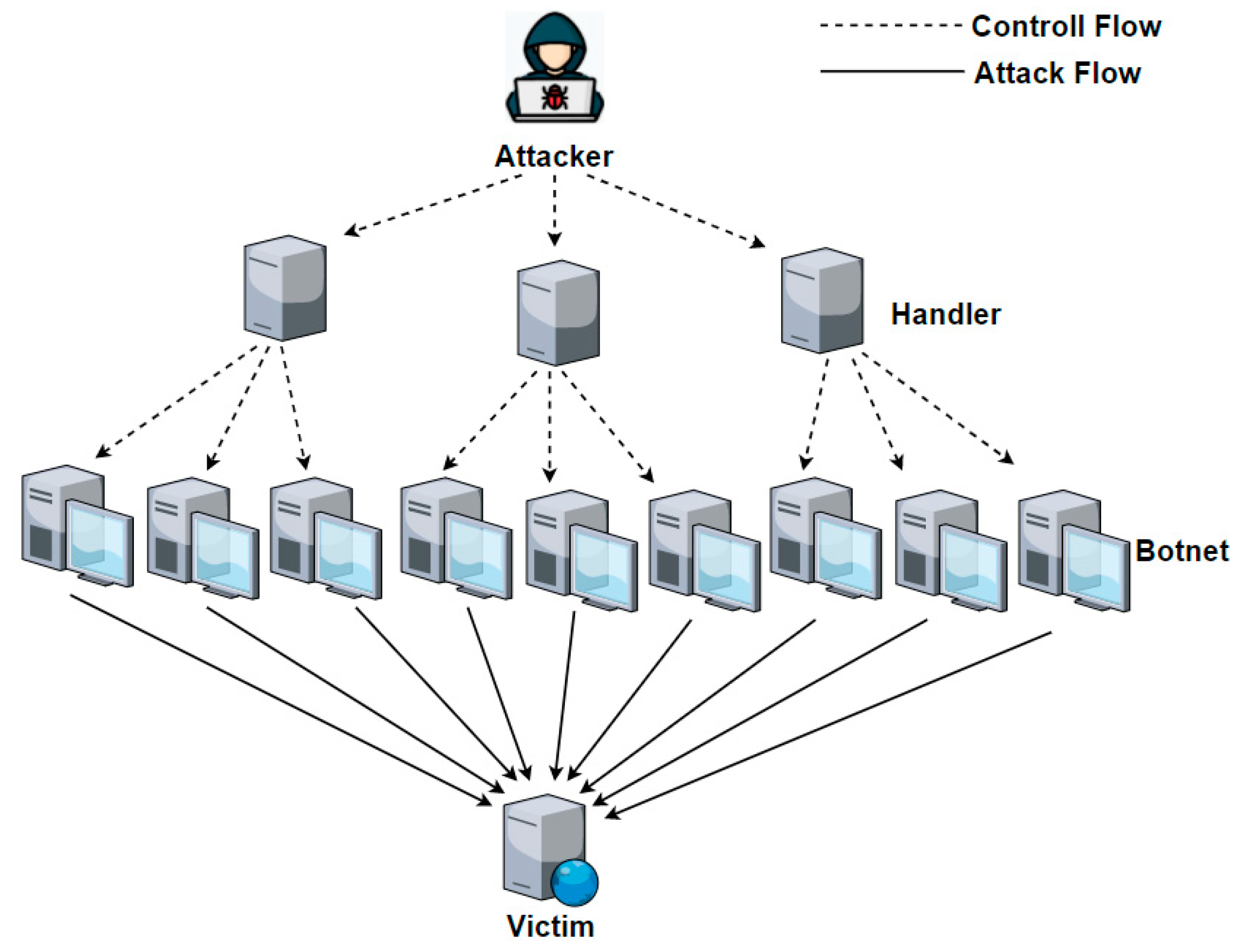
A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the availability of a network service or website by overwhelming it with a flood of traffic. Perpetrators use a network of compromised devices, often called a botnet, to send an enormous volume of requests to a target server, rendering it unable to respond to legitimate users.
DDoS attacks come in various forms, including UDP flood, SYN flood, and HTTP flood attacks. The attacker's goal is to exhaust the target's resources, such as bandwidth, CPU, or memory, causing downtime and financial losses.
Mitigating DDoS attacks involves deploying security measures like traffic filtering, rate limiting, and load balancing. Content delivery networks (CDNs) can also help distribute and absorb traffic, reducing the impact of an attack.
DDoS attacks can disrupt online services, leading to financial and reputational damage, making it crucial for organizations to invest in robust cybersecurity defenses to detect and mitigate these threats effectively.
You may be interested in these jobs
-

Barista/all Rounder
20 hours ago
Direct apply
Rudraman Ventures Ghaziabad, Uttar Pradesh, IndiaThis Job is for our Cafe in Crossing Republik by the name of "TWO MAD CHEF" · **Experience: · - ** 0 - 5 years · **Roles & Responsibilities: · - ** · - Greets every guest with a genuine smile and eye contact. · - Serves every product with smile and hospitality comment. · - Thank ...
-
Business Development Executive
2 days ago
Rohera Healthcare and Technology Private Limited New Delhi, India Full timeThe ideal candidate will have experience in all stages of the sales cycle. They should be confident with building new client relationship and maintaining existing ones. They should have evidence of strong skills and possess good negotiation skills. · Responsibilities · Build rel ...
-
Field Service Technician IV
6 days ago
Carrier Gurugram, India Full timeAbout the role · This role will be responsible to attend day to day complaints of Chillers. · Responsibilities · To attend day to day complaints of Chillers · Trouble shooting in chillers · To generate sales enquiry for spare part sale. · Minimum Requirements · 8-10+ years o ...


Comments